Team:Greensboro-Austin/Human Practices
From 2013.igem.org
| (66 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
{{Template:Greensboro-Austin/Stylesheet}} | {{Template:Greensboro-Austin/Stylesheet}} | ||
| - | + | __NOTOC__ | |
<html> | <html> | ||
| Line 7: | Line 7: | ||
<li class="team"><a href="/Team:Greensboro-Austin/Team" title="team"><span class="displace">Team</span></a></li> | <li class="team"><a href="/Team:Greensboro-Austin/Team" title="team"><span class="displace">Team</span></a></li> | ||
<li class="official_team_profile"><a href="https://igem.org/Team.cgi?year=2013&team_name=Greensboro-Austin" title="official_team_profile"><span class="displace">Official Team Profile</span></a></li> | <li class="official_team_profile"><a href="https://igem.org/Team.cgi?year=2013&team_name=Greensboro-Austin" title="official_team_profile"><span class="displace">Official Team Profile</span></a></li> | ||
| + | <li class="ncAAs"><a href="/Team:Greensboro-Austin/ncAAs" title="ncAAs"><span class="displace">ncAAs</span></a></li> | ||
<li class="MAPs"><a href="/Team:Greensboro-Austin/MAPs" title="MAPs"><span class="displace">MAPs</span></a></li> | <li class="MAPs"><a href="/Team:Greensboro-Austin/MAPs" title="MAPs"><span class="displace">MAPs</span></a></li> | ||
<li class="smell_degradation"><a href="/Team:Greensboro-Austin/Smell_degradation" title="smell_degradation"><span class="displace">Smell degradation</span></a></li> | <li class="smell_degradation"><a href="/Team:Greensboro-Austin/Smell_degradation" title="smell_degradation"><span class="displace">Smell degradation</span></a></li> | ||
| - | <li class=" | + | |
| + | <li class="bacto_art"><a href="/Team:Greensboro-Austin/Bacto-Art" title="bacto_art"><span class="displace">Bacto-Art</span></a></li> | ||
<li class="human_practices"><a href="/Team:Greensboro-Austin/Human_Practices" class="selected" title="Human Practices"><span class="displace">Human Practices</span></a></li> | <li class="human_practices"><a href="/Team:Greensboro-Austin/Human_Practices" class="selected" title="Human Practices"><span class="displace">Human Practices</span></a></li> | ||
| - | + | <li class="Standard_Proposal"><a href="/Team:Greensboro-Austin/Standard_Proposal" title="Standard_Proposal"><span class="displace">Standard_Proposal</span></a></li> | |
| - | + | ||
<li class="parts_submitted"><a href="/Team:Greensboro-Austin/Parts" title="parts_submitted"><span class="displace">Parts Submitted</span></a></li> | <li class="parts_submitted"><a href="/Team:Greensboro-Austin/Parts" title="parts_submitted"><span class="displace">Parts Submitted</span></a></li> | ||
<li class="notebook"><a href="/Team:Greensboro-Austin/Notebook" title="notebook"><span class="displace">Notebook</span></a></li> | <li class="notebook"><a href="/Team:Greensboro-Austin/Notebook" title="notebook"><span class="displace">Notebook</span></a></li> | ||
| + | <li class="safety"><a href="/Team:Greensboro-Austin/Safety" title="safety"><span class="displace">Safety</span></a></li> | ||
<li class="attributions"><a href="/Team:Greensboro-Austin/Team#Attributions" title="attributions"><span class="displace">Attributions</span></a></li> | <li class="attributions"><a href="/Team:Greensboro-Austin/Team#Attributions" title="attributions"><span class="displace">Attributions</span></a></li> | ||
| + | |||
| + | <!-- <li><img src="http://i.imgur.com/FBMrzYk.png" style="width:162.03px;height:567.6px"/></li> --> | ||
</ul> | </ul> | ||
<!--img src="https://static.igem.org/mediawiki/2012/1/16/University_of_texas_logo.jpg" alt="University of Texas at Austin logo" class="ut_logo" /--> | <!--img src="https://static.igem.org/mediawiki/2012/1/16/University_of_texas_logo.jpg" alt="University of Texas at Austin logo" class="ut_logo" /--> | ||
| + | |||
</html> | </html> | ||
| - | = | + | =Community Outreach= |
| + | [[File:Biosecurity workshop.png|400x|thumb|alt=fbi presentation|FBI Biosecurity Workshop]] | ||
| + | [[File:Article.jpg|400x|thumb|alt=Article.jpg|Press visits the lab]] | ||
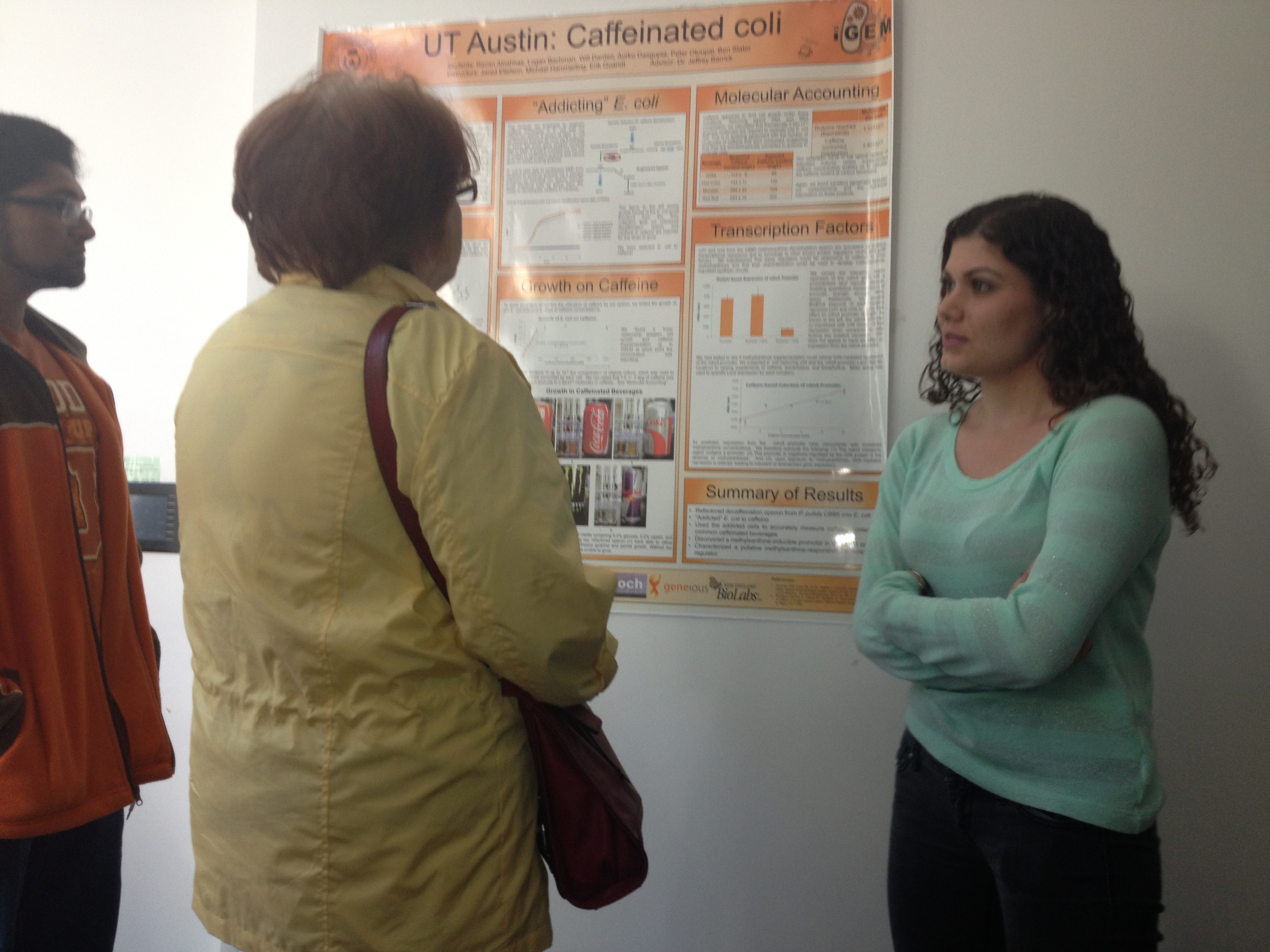
| + | [[File:Hotsciencecooltalks.JPG|400x|thumb|alt=Hotsciencecooltalks.JPG|Razan presents last years poster]] | ||
| + | A key principle of iGEM is education and outreach to the general public about synthetic biology. We invited a local paper -"The Daily Texan"- and a television crew from "TsTV" for a laboratory tour and were featured on the [http://www.youtube.com/watch?v=1Fvnnl4ZInA local news] and in a [http://www.dailytexanonline.com/news/2013/04/22/ut-students-work-on-entry-for-genetic-engineering-competition press release] detailing our daily activities in the lab. The team also sponsored a [http://www.dailytexanonline.com/2013/09/18/fbi-workshop-raises-awareness-against-biosecurity-threats FBI biosecurity workshop] attended by scientists, government officials, law enforcement, and members of the community. We fostered an environment of collaboration and transparency by bringing a diverse group of people together to discuss measures we can implement as a local community to ensure that synthetic biology is not used for harmful purposes. Finally, we presented last year's research on caffeine addicted bacteria at the popular science education event "Hot Science-Cool Talks". | ||
| + | <html> | ||
| + | <center> | ||
| + | <iframe width="560" height="315" src="//www.youtube.com/embed/1Fvnnl4ZInA" frameborder="0" allowfullscreen></iframe> | ||
| + | </center> | ||
| + | </html> | ||
| - | |||
| + | =Biosecurity= | ||
| + | [[File:ebola pic.jpg|300x|thumb|left|alt=The ebola virus, one of the most dangerous virons.|An electromicrograph of the ebola virus, one of the most dangerous virons.]] | ||
| + | [http://en.wikipedia.org/wiki/Bioterrorism Bioterrorism], in the form of synthetic biology, has become a much greater concern than it has is the past. It is now easier and cheaper to mass produce custom DNA than ever before. While this increases biological research exponentially, cheap and widely available genetic material creates opportunities for individuals and terrorist organizations to procure parts for the sake of creating an infectious agent or biological toxin. Currently, the government does not mandate that DNA synthesizing companies conduct precautionary screening measures to ensure that [http://en.wikipedia.org/wiki/Select_agent select agent] genes are not unknowingly produced and sold. Instead, the government only provides screening guidelines for potentially harmful oligonucleotides and do not enforce them. If these regulations are not enforced and updated, a "perfect storm" could occur and, at the very least, turn public ignorance of synthetic biology into abhorrence. [[#References|[1]]] | ||
| + | <br><br> | ||
| + | ==Motivation== | ||
| - | + | At last year's iGEM competition, our team attended a presentation on biosecurity by Edward You of the FBI. At this presentation, we learned that DNA synthesis companies currently screen double-stranded DNA orders for matches to a select agent database, but do not screen oligonucleotide orders in the same way. This was confirmed in a similar presentation at SB6.0 and at our [http://fbi-abw.eventbrite.com/ FBI Biosecurity workshop]. We found this information troubling, as any competent molecular biologist can easily use the same techniques that DNA synthesis companies such as IDT use to synthesize large pieces of double-stranded DNA from oligos. When asked, representatives indicated that it would be too expensive and too resource intensive to screen oligo orders against a pathogen database. We believed that it should be possible to develop algorithms to cleverly detect oligo orders that are intended to construct select agents in such a way that minimizes false positives. We sought to develop such an algorithm, and to communicate the importance of such screening to the synthetic biology community and to relevant government agencies. | |
| - | |||
| - | |||
| - | |||
| - | |||
| - | |||
| - | |||
| - | |||
| - | |||
| - | |||
| - | |||
==Background== | ==Background== | ||
| + | The Select Agents and Toxins list is composed of harmful bacteria, viruses, and toxins that the Department of Health and Safety is most concerned may be used as weapons for bioterrorism. [[#References|[2]]] Various oligo screening methods have been developed such as [http://guidance.tau.ac.il/overview.html Guidance], Top Homology, and Best Match. Best Match, though less fool proof than other screening algorithms, like Top Homology, is the more popular screening method chosen by synthesizing companies due to it being much more efficient and compartmentalized. When an oligo is ordered, the sequence is screened for homology to any unique sequence of the Select Agents and Toxins. Best Match screens 200 base pairs at a time and screens using different reading frames. If the oligo is more homologous to a Select Agent or Toxin than any other sequence found in international sequence reference databanks, such as NCBI, the order is flagged. The owner of the account must disclose their purpose for ordering such an oligo and must be granted permission to have a dangerous oligo synthesized. | ||
| + | IGSC ([http://www.genesynthesisconsortium.org/ International Gene Synthesis Consortium]) affiliated companies screen ordered oligos as six different reading frames. The amino acid sequences (if present) are screened for protein similarity in a Regulated Pathogen Database. The Regulated Pathogen Database is continually modified and is composed from the Select Agents list, the Australian Group list, and other regulated pathogens and toxins set by various countries. [[#References|[3]]] | ||
| - | + | There are various inadequacies with Best Match. One example is that Best Match is not able to detect unrelated accounts conspiring to order harmful oligos. Another is that Best Match does not catch oligos that are not the best match. For instance, a user could order an oligo encoding a modified select agent sequence. This sequence would not be caught by a Best Match search because the oligo could be designed to be more homologous towards a non pathogenic sequence. Additionally, the Select Agents and Toxins list does not account for every harmful agent and toxin. Thus, harmful oligos that are not listed could be synthesized because they are simply not screened for. Forbidden oligos are distributed to government, university, non-profit, and industry researchers and are tightly regulated by companies adhering to screening protocols, like IGSC companies, but, as previously mentioned, are not enforced. [[#References|[3]]] | |
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
==Project== | ==Project== | ||
| - | + | We developed a conceptual computational procedure for screening oligonucleotide orders against a pathogen database. We explored algorithmic strategies to create a nucleotide database and query it using BLAST+ to search for homologous virulent sequences. The program was constructed using the python libraries: biopython and matplotlib and was simple to implement. | |
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
==References== | ==References== | ||
| - | # | + | # Federal Register/Vol. 74, No. 227/Friday, November 27, 2009/Notices |
| + | # HHS AND USDA SELECT AGENTS AND TOXINS 7 CFR Part 331 , 9 CFR Part 121 , and 42 CFR Part 73. (n.d.)., 331. | ||
| + | # IGSC-Harmonized-Screening-Protocol | ||
# Bucher, J. R. (2009). ACTION :, 74(227), 38–46. | # Bucher, J. R. (2009). ACTION :, 74(227), 38–46. | ||
# Framework, S. (2011). correspondence Strengths and limitations of the federal guidance on synthetic DNA, 29(3), 1–3. doi:10.1038/nbt0311-208 | # Framework, S. (2011). correspondence Strengths and limitations of the federal guidance on synthetic DNA, 29(3), 1–3. doi:10.1038/nbt0311-208 | ||
| - | # | + | # Han, Z., Boshra, H., Sunyer, J. O., Zwiers, S. H., Paragas, J., Harty, R. N., Han, Z., et al. (2003). Biochemical and Functional Characterization of the Ebola Virus VP24 Protein : Implications for a Role in Virus Assembly and Budding Biochemical and Functional Characterization of the Ebola Virus VP24 Protein : Implications for a Role in Virus Assembly and Budding. doi:10.1128/JVI.77.3.1793 |
# No Title. (n.d.)., 45–49. | # No Title. (n.d.)., 45–49. | ||
# Preventing the misuse of gene synthesis Commercialized GM crops and yield. (2009)., 27(9), 800–801. | # Preventing the misuse of gene synthesis Commercialized GM crops and yield. (2009)., 27(9), 800–801. | ||
# Schmidt, M., & Giersch, G. (2011). Dna s s, 1–15. | # Schmidt, M., & Giersch, G. (2011). Dna s s, 1–15. | ||
# Select, F., & Program, A. (n.d.). Restricted Experiment Guidance Document, (Cdc). | # Select, F., & Program, A. (n.d.). Restricted Experiment Guidance Document, (Cdc). | ||
| - | |||
| - | |||
Latest revision as of 03:49, 28 September 2013
Community Outreach
A key principle of iGEM is education and outreach to the general public about synthetic biology. We invited a local paper -"The Daily Texan"- and a television crew from "TsTV" for a laboratory tour and were featured on the [http://www.youtube.com/watch?v=1Fvnnl4ZInA local news] and in a [http://www.dailytexanonline.com/news/2013/04/22/ut-students-work-on-entry-for-genetic-engineering-competition press release] detailing our daily activities in the lab. The team also sponsored a [http://www.dailytexanonline.com/2013/09/18/fbi-workshop-raises-awareness-against-biosecurity-threats FBI biosecurity workshop] attended by scientists, government officials, law enforcement, and members of the community. We fostered an environment of collaboration and transparency by bringing a diverse group of people together to discuss measures we can implement as a local community to ensure that synthetic biology is not used for harmful purposes. Finally, we presented last year's research on caffeine addicted bacteria at the popular science education event "Hot Science-Cool Talks".
Biosecurity
[http://en.wikipedia.org/wiki/Bioterrorism Bioterrorism], in the form of synthetic biology, has become a much greater concern than it has is the past. It is now easier and cheaper to mass produce custom DNA than ever before. While this increases biological research exponentially, cheap and widely available genetic material creates opportunities for individuals and terrorist organizations to procure parts for the sake of creating an infectious agent or biological toxin. Currently, the government does not mandate that DNA synthesizing companies conduct precautionary screening measures to ensure that [http://en.wikipedia.org/wiki/Select_agent select agent] genes are not unknowingly produced and sold. Instead, the government only provides screening guidelines for potentially harmful oligonucleotides and do not enforce them. If these regulations are not enforced and updated, a "perfect storm" could occur and, at the very least, turn public ignorance of synthetic biology into abhorrence. [1]
Motivation
At last year's iGEM competition, our team attended a presentation on biosecurity by Edward You of the FBI. At this presentation, we learned that DNA synthesis companies currently screen double-stranded DNA orders for matches to a select agent database, but do not screen oligonucleotide orders in the same way. This was confirmed in a similar presentation at SB6.0 and at our [http://fbi-abw.eventbrite.com/ FBI Biosecurity workshop]. We found this information troubling, as any competent molecular biologist can easily use the same techniques that DNA synthesis companies such as IDT use to synthesize large pieces of double-stranded DNA from oligos. When asked, representatives indicated that it would be too expensive and too resource intensive to screen oligo orders against a pathogen database. We believed that it should be possible to develop algorithms to cleverly detect oligo orders that are intended to construct select agents in such a way that minimizes false positives. We sought to develop such an algorithm, and to communicate the importance of such screening to the synthetic biology community and to relevant government agencies.
Background
The Select Agents and Toxins list is composed of harmful bacteria, viruses, and toxins that the Department of Health and Safety is most concerned may be used as weapons for bioterrorism. [2] Various oligo screening methods have been developed such as [http://guidance.tau.ac.il/overview.html Guidance], Top Homology, and Best Match. Best Match, though less fool proof than other screening algorithms, like Top Homology, is the more popular screening method chosen by synthesizing companies due to it being much more efficient and compartmentalized. When an oligo is ordered, the sequence is screened for homology to any unique sequence of the Select Agents and Toxins. Best Match screens 200 base pairs at a time and screens using different reading frames. If the oligo is more homologous to a Select Agent or Toxin than any other sequence found in international sequence reference databanks, such as NCBI, the order is flagged. The owner of the account must disclose their purpose for ordering such an oligo and must be granted permission to have a dangerous oligo synthesized.
IGSC ([http://www.genesynthesisconsortium.org/ International Gene Synthesis Consortium]) affiliated companies screen ordered oligos as six different reading frames. The amino acid sequences (if present) are screened for protein similarity in a Regulated Pathogen Database. The Regulated Pathogen Database is continually modified and is composed from the Select Agents list, the Australian Group list, and other regulated pathogens and toxins set by various countries. [3]
There are various inadequacies with Best Match. One example is that Best Match is not able to detect unrelated accounts conspiring to order harmful oligos. Another is that Best Match does not catch oligos that are not the best match. For instance, a user could order an oligo encoding a modified select agent sequence. This sequence would not be caught by a Best Match search because the oligo could be designed to be more homologous towards a non pathogenic sequence. Additionally, the Select Agents and Toxins list does not account for every harmful agent and toxin. Thus, harmful oligos that are not listed could be synthesized because they are simply not screened for. Forbidden oligos are distributed to government, university, non-profit, and industry researchers and are tightly regulated by companies adhering to screening protocols, like IGSC companies, but, as previously mentioned, are not enforced. [3]
Project
We developed a conceptual computational procedure for screening oligonucleotide orders against a pathogen database. We explored algorithmic strategies to create a nucleotide database and query it using BLAST+ to search for homologous virulent sequences. The program was constructed using the python libraries: biopython and matplotlib and was simple to implement.
References
- Federal Register/Vol. 74, No. 227/Friday, November 27, 2009/Notices
- HHS AND USDA SELECT AGENTS AND TOXINS 7 CFR Part 331 , 9 CFR Part 121 , and 42 CFR Part 73. (n.d.)., 331.
- IGSC-Harmonized-Screening-Protocol
- Bucher, J. R. (2009). ACTION :, 74(227), 38–46.
- Framework, S. (2011). correspondence Strengths and limitations of the federal guidance on synthetic DNA, 29(3), 1–3. doi:10.1038/nbt0311-208
- Han, Z., Boshra, H., Sunyer, J. O., Zwiers, S. H., Paragas, J., Harty, R. N., Han, Z., et al. (2003). Biochemical and Functional Characterization of the Ebola Virus VP24 Protein : Implications for a Role in Virus Assembly and Budding Biochemical and Functional Characterization of the Ebola Virus VP24 Protein : Implications for a Role in Virus Assembly and Budding. doi:10.1128/JVI.77.3.1793
- No Title. (n.d.)., 45–49.
- Preventing the misuse of gene synthesis Commercialized GM crops and yield. (2009)., 27(9), 800–801.
- Schmidt, M., & Giersch, G. (2011). Dna s s, 1–15.
- Select, F., & Program, A. (n.d.). Restricted Experiment Guidance Document, (Cdc).
 "
"